HTB Certified Defensive Security Analyst certification review
Who is it for ?
HTB CDSA is one of the most comprehensive certifications targeted towards beginner and even intermediate SOC analysts. Passing the certification proves the candidates ability in conducting a rigerous security incident investigation using tools like SIEM and using Digital Forensics. According to the official HTB CDSA exam page, this certification is targeted towards :
- Entry level Security Analysts
- Entry level SOC Analysts
- Entry level Incident Handlers
- Entry level Forensics Analysts
- Penetration Testers
- IT Administrators
- IT Security Personnel
Prerequisites
Hack The Box mandates all candidates to finish the whole SOC Analyst path completely within their academy platform in order to be eligible to even take the exam and this is a great way to enhance the learning experience and make sure everyone goes through the same learning experience before taking the exam. There is even a prerequisites path before going through the SOC analyst path for those who want to first grasp the basics like Networking, Active Directory Basics and even topics like powershell before going through that path since it assumes knowledge in those fundamentals. The topics covered in the SOC Analyst pre-requisites path include :
- Linux Fundamentals
- Introduction to Bash Scripting
- Windows Fundamentals
- Introduction to Windows Command Line
- Introduction to Networking
- Introduction to Active Directory
- Web Requests
- Penetration Testing Process
- Network Enumeration with Nmap
- Intro to Assembly Language
Personally I only needed to finish the Active Directory basics path since the main path is very AD intensive especially with the modules diving through AD attacks and defenses. Additionally I didn’t have that much knowledge in Powershell or Bash scripting which are covered in the pre-requisites modules but when going through the modules that have these involved I encourage not being afraid to research the internet in case you got stuck to grasp new concept quickly as the path is very intensive with lots of new information especially for newcomers. However, keep in mind this is only a special case as everyone have their own background and knowledge beforehand so consider checking this pre-requisite path beforehand and be honest with yourself ! 
Exam Prep …
Spoiler alert .... TAKE NOTES !
I started going through the SOC Analyst path as someone who haven’t done much blue teaming activities since this is my very first blue teaming certification. The path took me roughly about 7 months to finish due to being busy with college and internships but I’d say it’s possible to finish in roughly 3 months if anyone dedicates about 20 hours per week consistently. Most important part is writing precise notes so you can come back to later even if its months after. I personally used Notion for note taking and I heavily recommend it.
The main path covers the following topics :
- Incident Handling Process
- Security Monitoring & SIEM Fundamentals
- Windows Event Logs & Finding Evil
- Introduction to Threat Hunting & Hunting With Elastic
- Understanding Log Sources & Investigating with Splunk
- Windows Attacks & Defense
- Intro to Network Traffic Analysis
- Intermediate Network Traffic Analysis
- Working with IDS/IPS
- Introduction to Malware Analysis
- JavaScript Deobfuscation
- YARA & Sigma for SOC Analysts
- Introduction to Digital Forensics
- Detecting Windows Attacks with Splunk
- Security Incident Reporting
A lot of people will find the path overwhelming due to the vast amount of topics covered but I encourage not rushing it and taking it slowly to help let the knowledge sink in. The path will teach you a great deal of skills that will make you a qualified and an attractive SOC analyst for the different enterprises. You will learn how to sift through the security logs and identify attack patterns using SIEMs like Splunk and Elastic, in addition to vital skills like Threat Hunting, DFIR, Malware Analysis, utilizing YARA and Sigma detection rules (I love this module!), dealing with IDS and IPS and most importantly how to compose a professional security incident report. Keep in mind the path encourages researching and thinking out of the box as all the labs given must be solved and a lot will make you actually think twice! Overall it’s a very rewarding experience and the feeling if nailing the whole path exercises and labs is worth the grind.
I did and passed the eJPTv2 exam before taking this certfication and let me tell you if you want to have a great advantage I heavily advise having some good red teaming background as the whole path talks about detecting and responding to attacks. So that red teaming and pentesting knowledge will help give you some great perspective and insight about what’s going on when reading those logs.
After you are done with the whole path you will be eligible to buy an exam voucher and attempt the exam. That’s where your notes will now come on your favour. Make sure to re-read these notes and grasp all the concepts especially with the topics you find yourself weak in. Blindly doing the labs again for the topics you feel not so capable of is a great way to gain confidence and this will help you become fluent in the exam environment as you will immediately know what to do once you are in. I also encourage solving a bunch of Sherlocks especially the SOC and DFIR ones. I personally did the following Sherlocks :
- Noxious (SOC-Very Easy)
- Brutus (DFIR-Very Easy)
- Meerkat (SOC-Easy)
- RogueOne (DFIR-Easy)
- Logjammer (DFIR-Easy)
- Heartbreaker (DFIR-Medium)
- APTNightmare (DFIR-Medium)
A lot of the Sherlocks will feel out of topic and covering new concept but they will help give you that think out of the box mindset which is very important in the exam environment. Additionally, doing Splunk BOTS really helped me test my skills in performing a full investigation with Splunk and that makes it a great test after you are done with the path. Just make sure to do it fully and blindly without reading any writeups. All of this practise will pay off at the exam.
Pricing
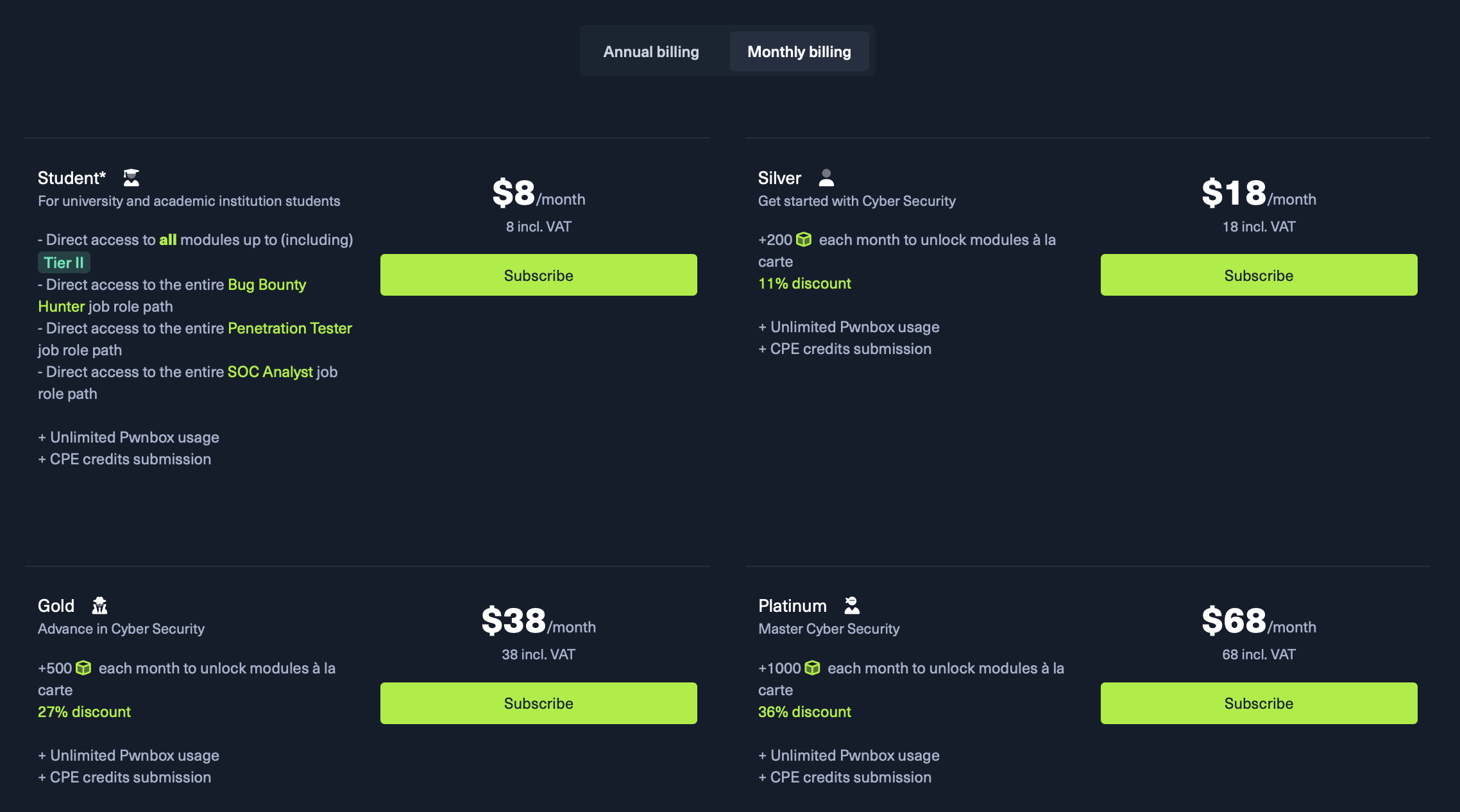
The SOC Analyst path is available at HTB Academy platform and fortunately there are multiple afforable subscription models for different users. I used their student subscription which is only $8 per months if you have a .edu email. This will give you access to all the modules in the SOC Analyst path, the pre-requisites path and even access to all their main certifications paths (CPTS, CBBH and CDSA).
If you don’t have a .edu email fortunately there are some other affordable subscriptions like the Platinum sub which costs around $68 and gives you 1000 cubes enough to cover and unlock most of the modules in the path. The whole path costs around 1220 cubes so a single Platinum subscription ($68) and an additional Silver Subscription ($18) will be enough to unlock the whole path.
You will get additional more cubes after you finish each module completely.
The exam voucher costs around $210 so overall the certification will cost you around $296 which is much more affordable than other blue teaming certifications like Blue Team level 1 ($485) and Cyberdefenders CCD ($800). HTB CDSA is also very comprehensive and is on par with CCD in terms of difficulty, making it a big bang for your buck !
Exam Experience
I never really felt fully prepared for the exam even after going through all the previously mentioned prep steps. However, I eventually had the courage to just press that Start Exam button and get my hands dirty since a lot of people told me that finishing the whole path alone even without doing sherlocks or additional 3rd party prep material makes you fully qualified to pass the exam.
Upon starting the exam you will be provided with everything you need to pass including the letter of engagement as well as the exam lab environment. You will have the choice to either use the Pwnbox or using the exam VPN to access the lab. I personally found the VPN ideal as I can just connect directly using my own machine.
 According to the sysreptor exam report template there will be 2 incidents for the exam. The first one includes 20 flags in which only 17 are required. For both the first and the second incident you are required to compose a commercial grade exam report which meticulously documents all the investigation steps and conclusions for both incidents.
According to the sysreptor exam report template there will be 2 incidents for the exam. The first one includes 20 flags in which only 17 are required. For both the first and the second incident you are required to compose a commercial grade exam report which meticulously documents all the investigation steps and conclusions for both incidents.
I highly encourage taking screenshots of everything important you observe at the exam environment and write all commands or SIEM queries you used for any step that ultimately led or helped getting a certain flag (as outlined in the sysreptor Exam Objectives). This will make the report writing step a lot more manageable and less stressful as it saved a ton of time.
With all that being said I was able to get all the flags on my 3rd exam day and this gave me a confidence boost to start composing the report. Sysreptor was a life saver during this phase as it made report writing a lot easier and straight forward. After composing a decent report draft for incident 1 all that’s left is to through incident 2 and finish my report. I had to use the full 7 days to make sure I covered everything for both incidents in my report and that was in continuous reference to the security incident report sample found in the Security Incident Reporting module.
After submitting my report it took less than 20 business days for me to get my results as promised by their conditions. I finally got an email congratulating me on passing the CDSA exam and it felt so good to conclude my 7 months exam prep journey with a pass !  Overall, I highly recommend anyone who’s looking into becoming a SOC analyst or even just getting better at SOC operations to get that certification. It’s highly practical, very comprehensive and like most Hack The Box content reflects their well tailored, well crafted and high quality content.
Overall, I highly recommend anyone who’s looking into becoming a SOC analyst or even just getting better at SOC operations to get that certification. It’s highly practical, very comprehensive and like most Hack The Box content reflects their well tailored, well crafted and high quality content.